(This article is currently a work-in-progress. As of 12.04.2009, it includes the rationale for how one might use a VPN, but does not yet include the configuration and setup details, because they are currently incomplete.)
Rationale
This HOWTO explains how one might use OpenVPN to avoid the security and privacy risks associated with web-browsing from an untrusted wireless connection and/or using an untrusted Internet Service Provider. The situation is as follows:
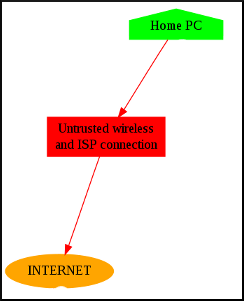
The presence of the untrusted elements opens one to the risk of internet traffic interception, resulting in loss of personal data, passwords, interception or logging of email and web traffic and so on. For a full discussion of the very real risks, see this post.
Requirements
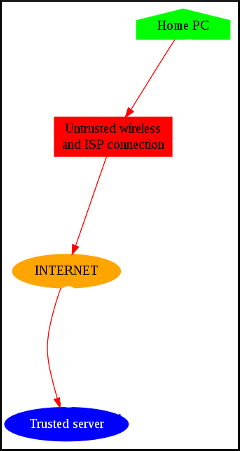
This HOWTO relies on a single additional element, namely a trusted server somewhere “out there” on the Internet. The nature of this server does not affect the details of this HOWTO, so long as the following is true:
– One has root access to said server and it is running some Linux-based distribution;
– One trusts the company providing or hosting said server more than your home ISP.
In my case, a virtual machine from Bytemark fits the bill perfectly. It’s running Debian and my notes are based on that distribution; modifications may be required for other distros. So, our network plan is now:
Background
We will creating a virtual private network (VPN) to connect our home PC to the server, resulting in the tunneling and encrypting of all network traffic to the trusted server. Anyone sniffing the wireless traffic or intercepting the traffic at our ISP will see only encrypted packets of data flying back and forth. They will be aware that you are using a VPN, but the contents of your traffic cannot be seen. Further ‘upstream’ on The Internet, your traffic will appear to be emerging from your trusted server, rather than your home connection. This is the full plan:
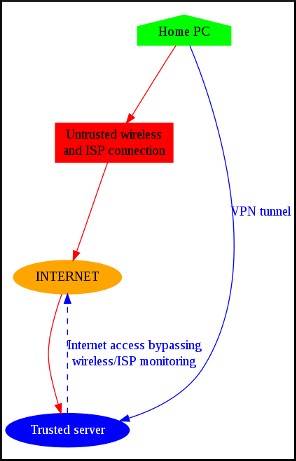
(Setup and configuration: work-in-progress)
